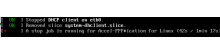
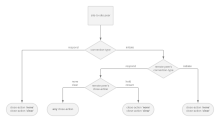
Not sure if this is relevant to the task.
But once when shutting down a VM with VyOS 1.3.1-S1, it took a long time to shut down:
- Feed Queries
- All Stories
- Search
- Feed Search
- Transactions
- Transaction Logs
All Stories
Jun 3 2022
Should I make improvements to the remaining revisions in the PR?
Sorry I just saw it now, I'll test it. But because of limited conditions, I may test in the future, please forgive me
In T3435#115394, @n.fort wrote:Error still present on VyOS 1.4-rolling-202201020317
vyos@vyos:~$ show nat source rules Traceback (most recent call last): File "/usr/libexec/vyos/op_mode/show_nat_rules.py", line 114, in <module> print(format_nat_rule.format(rule, srcdests[0], tran_addr, interface)) IndexError: list index out of range Rule Source Translation Outbound Interface ---- ------ ----------- ------------------ vyos@vyos:~$ show ver Version: VyOS 1.4-rolling-202201020317 Release train: sagittaNat config in this example:
vyos@vyos:~$ show config comm | grep nat set nat source rule 10 description 'Masquerade to NAT' set nat source rule 10 outbound-interface 'eth0' set nat source rule 10 translation address 'masquerade'
Jun 2 2022
@m.korobeinikov I believe that I already posted this some time ago, but just in case...
Not all combinations of DPD and close-action are safe. Actually, most of them sooner or later will lead to issues with IPSec. So, I created the next scheme. It is from 2020, so I will not say that nothing was changed from that time, however, it shows well how careful you should be while configuring IPSec. On the scheme, you can see the only safe configuration of the close-action option, depending on how the peer is configured, but the same logic can be applied to DPD.
PR https://github.com/vyos/vyos-build/pull/240
disable owamp|twamp.service by default
@SrividyaA will be present in the next rolling release
PR for the current https://github.com/vyos/vyos-1x/pull/1346
In T973#124168, @superq wrote:I wouldn't call telegraf a very good option. It does a very bad job of producing Prometheus metrics.
For Debian11 requires pkg "libpam-tacplus" that is not available https://github.com/kravietz/pam_tacplus/issues/180
I wouldn't call telegraf a very good option. It does a very bad job of producing Prometheus metrics.
Prometheus-client already in 1.4
https://docs.vyos.io/en/latest/configuration/service/monitoring.html#prometheus-client
Jun 1 2022
May 31 2022
Yes on this version it is available the requested options for ipv6:
yes, it was added on this version vyos-1.4-rolling-202205311706, please check again
I just check and on version: vyos-1.4-rolling-202205310217 is still missing :(
We've added this feature in our latest nightly building release, could you check it ?
Has any progress on this been made? I am still having this issue on 1.4-rolling-202205250217.
May 30 2022
PR for op-mode importing existing PKI files into config: https://github.com/vyos/vyos-1x/pull/1343
May 29 2022
This vm started out with 4G of memory and 2CPUs; I doubled quickly everything when I hit the out of memory error the first time, but that didn't help. I can quickly install the latest rolling and test
Yes, you error with "root" user is a known issue: T4281.
Reset added in T4442
Currently dealing with some minor FRR issues:
I've debugged this further, by breaking up my configuration into various sections (system, interfaces, firewall,nat,service,vpn etc) and running them on a new VM.
Still not much luck here. But I've let the boot run a bit longer, and notice the following:
May 28 2022
@fernando Could you try to set sysctl mark?
sysctl -w net.ipv4.conf.eth0.src_valid_mark=1 sysctl -w net.ipv4.conf.eth1.src_valid_mark=1
PR https://github.com/vyos/vyos-1x/pull/1340
set service event-handler event first filter pattern '.*ssh2.*' set service event-handler event first script arguments '192.0.2.5' set service event-handler event first script environment interface value 'eth0' set service event-handler event first script path '/config/scripts/hello.sh'
The current salt-minion version 3003.4+ds-1
@maznu Do we need anything else for it?
Okay, thats the only rule where I was using a port-group combined with protocol all; the others that use protocol all dont have a port or port group in the rule, so they are okay?
May 27 2022
PR for 1.4 Sagitta branch https://github.com/vyos/vyos-1x/pull/1337
Works on my setup
In T1230#123939, @panachoi wrote:1.4 rolling does not help me, so there must be something "wrong" with my configuration. I've attached the private config, it would be awesome if someone might find what's broken.
private.cfg127 KBDownload