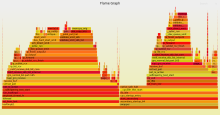
Flame graph for 1.3-rc4, proxmox/virtio
- Feed Queries
- All Stories
- Search
- Feed Search
- Transactions
- Transaction Logs
Jun 17 2021
Jun 15 2021
Jun 11 2021
Jun 10 2021
@krox2 How should looks like a configuration for many local/remote traffic selectors per one vti interface?
Should be fixed with commit https://github.com/vyos/vyos-build/commit/7905f0d5715bb8da158d09734ba78dc28b2fd4e1
I can't reproduce it, VyOS 1.3-beta-202106081558
set policy prefix-list FOO rule 10 action 'permit' set policy prefix-list FOO rule 10 prefix '0.0.0.0/0' set policy route-map FOO rule 10 action 'permit' set policy route-map FOO rule 10 match ip address prefix-list 'FOO' set policy route-map FOO rule 10 set distance '220' set policy route-map FOO rule 1000 action 'permit'
Commit with such policies:
vyos@r4-1.3# time commit
Jun 9 2021
@n.fort You can try to replace True with False there (1.3 and 1.4). But it needs more tests. In some cases, it was some bugs with the DHCP server and not the primary address.
https://github.com/vyos/vyos-1x/blob/5d068442cf7b1863724c83168176ce2940a023fe/src/conf_mode/dhcp_server.py#L237
It may be problem with large prefix-lists T2425
Try to check the same directly in the FRR.
VyOS 1.3-beta-202106081558
Works as expected.
Jun 9 19:57:38 r4-1 charon: 13[CFG] no IKE_SA named 'peer-192.0.2.2-tunnel-0' found
Jun 9 19:57:38 r4-1 charon: 14[CFG] received stroke: initiate 'peer-192.0.2.2-tunnel-0'
Jun 9 19:57:38 r4-1 charon: 06[IKE] <peer-192.0.2.2-tunnel-0|4> initiating Main Mode IKE_SA peer-192.0.2.2-tunnel-0[4] to 192.0.2.2
Jun 9 19:57:38 r4-1 charon: 06[ENC] <peer-192.0.2.2-tunnel-0|4> generating ID_PROT request 0 [ SA V V V V V ]
Jun 9 19:57:38 r4-1 charon: 06[NET] <peer-192.0.2.2-tunnel-0|4> sending packet: from 192.0.2.1[500] to 192.0.2.2[500] (180 bytes)
Jun 9 19:57:38 r4-1 charon: 07[NET] <peer-192.0.2.2-tunnel-0|4> received packet: from 192.0.2.2[500] to 192.0.2.1[500] (160 bytes)
Jun 9 19:57:38 r4-1 charon: 07[ENC] <peer-192.0.2.2-tunnel-0|4> parsed ID_PROT response 0 [ SA V V V V ]
Jun 9 19:57:38 r4-1 charon: 07[IKE] <peer-192.0.2.2-tunnel-0|4> received XAuth vendor ID
Jun 9 19:57:38 r4-1 charon: 07[IKE] <peer-192.0.2.2-tunnel-0|4> received DPD vendor ID
Jun 9 19:57:38 r4-1 charon: 07[IKE] <peer-192.0.2.2-tunnel-0|4> received FRAGMENTATION vendor ID
Jun 9 19:57:38 r4-1 charon: 07[IKE] <peer-192.0.2.2-tunnel-0|4> received NAT-T (RFC 3947) vendor ID
Jun 9 19:57:38 r4-1 charon: 07[CFG] <peer-192.0.2.2-tunnel-0|4> selected proposal: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Jun 9 19:57:38 r4-1 charon: 07[ENC] <peer-192.0.2.2-tunnel-0|4> generating ID_PROT request 0 [ KE No NAT-D NAT-D ]
Jun 9 19:57:38 r4-1 charon: 07[NET] <peer-192.0.2.2-tunnel-0|4> sending packet: from 192.0.2.1[500] to 192.0.2.2[500] (244 bytes)
Jun 9 19:57:38 r4-1 charon: 05[NET] <peer-192.0.2.2-tunnel-0|4> received packet: from 192.0.2.2[500] to 192.0.2.1[500] (244 bytes)
Jun 9 19:57:38 r4-1 charon: 05[ENC] <peer-192.0.2.2-tunnel-0|4> parsed ID_PROT response 0 [ KE No NAT-D NAT-D ]
Jun 9 19:57:38 r4-1 charon: 05[ENC] <peer-192.0.2.2-tunnel-0|4> generating ID_PROT request 0 [ ID HASH N(INITIAL_CONTACT) ]
Jun 9 19:57:38 r4-1 charon: 05[NET] <peer-192.0.2.2-tunnel-0|4> sending packet: from 192.0.2.1[500] to 192.0.2.2[500] (108 bytes)
Jun 9 19:57:38 r4-1 charon: 08[NET] <peer-192.0.2.2-tunnel-0|4> received packet: from 192.0.2.2[500] to 192.0.2.1[500] (76 bytes)
Jun 9 19:57:38 r4-1 charon: 08[ENC] <peer-192.0.2.2-tunnel-0|4> parsed ID_PROT response 0 [ ID HASH ]
Jun 9 19:57:38 r4-1 charon: 08[IKE] <peer-192.0.2.2-tunnel-0|4> IKE_SA peer-192.0.2.2-tunnel-0[4] established between 192.0.2.1[192.0.2.1]...192.0.2.2[192.0.2.2]
Jun 9 19:57:38 r4-1 charon: 08[IKE] <peer-192.0.2.2-tunnel-0|4> scheduling reauthentication in 2524s
Jun 9 19:57:38 r4-1 charon: 08[IKE] <peer-192.0.2.2-tunnel-0|4> maximum IKE_SA lifetime 3064s
Jun 9 19:57:38 r4-1 charon: 08[ENC] <peer-192.0.2.2-tunnel-0|4> generating QUICK_MODE request 364019988 [ HASH SA No KE ID ID ]
Jun 9 19:57:38 r4-1 charon: 08[NET] <peer-192.0.2.2-tunnel-0|4> sending packet: from 192.0.2.1[500] to 192.0.2.2[500] (316 bytes)
Jun 9 19:57:38 r4-1 charon: 09[NET] <peer-192.0.2.2-tunnel-0|4> received packet: from 192.0.2.2[500] to 192.0.2.1[500] (316 bytes)
Jun 9 19:57:38 r4-1 charon: 09[ENC] <peer-192.0.2.2-tunnel-0|4> parsed QUICK_MODE response 364019988 [ HASH SA No KE ID ID ]
Jun 9 19:57:38 r4-1 charon: 09[CFG] <peer-192.0.2.2-tunnel-0|4> selected proposal: ESP:AES_CBC_256/HMAC_SHA1_96/MODP_1024/NO_EXT_SEQ
Jun 9 19:57:38 r4-1 charon: 09[IKE] <peer-192.0.2.2-tunnel-0|4> CHILD_SA peer-192.0.2.2-tunnel-0{1} established with SPIs cb0aa83a_i c728156c_o and TS 10.1.0.0/24 === 10.2.3.0/24
Jun 9 19:57:38 r4-1 charon: 09[ENC] <peer-192.0.2.2-tunnel-0|4> generating QUICK_MODE request 364019988 [ HASH ]
Jun 9 19:57:38 r4-1 charon: 09[NET] <peer-192.0.2.2-tunnel-0|4> sending packet: from 192.0.2.1[500] to 192.0.2.2[500] (60 bytes)
vyos@r4-1.3:~$Ok it already fixed in 1.3 T2916 and can be migrated to crux
Jun 8 2021
It seems Arp monitor not supported in 802.3ad mode
It is redirected from
http://archive.repo.saltstack.com/apt/debian/8/amd64/2017.7
to
https://archive.repo.saltproject.io/apt/debian/8/amd64/2017.7
Jun 7 2021
PR https://github.com/vyos/vyos-build/pull/169
Jun 8 00:59:20 r1-roll ipsec_starter[2373]: charon (2374) started after 400 ms
Jun 8 00:59:20 r1-roll charon: 05[CFG] received stroke: add connection 'peer-192.0.2.2-tunnel-0'
Jun 8 00:59:20 r1-roll charon: 05[CFG] added configuration 'peer-192.0.2.2-tunnel-0'
Jun 8 00:59:20 r1-roll charon: 07[CFG] received stroke: initiate 'peer-192.0.2.2-tunnel-0'
Jun 8 00:59:20 r1-roll charon: 07[IKE] <peer-192.0.2.2-tunnel-0|1> initiating Main Mode IKE_SA peer-192.0.2.2-tunnel-0[1] to 192.0.2.2
Jun 8 00:59:20 r1-roll charon: 07[ENC] <peer-192.0.2.2-tunnel-0|1> generating ID_PROT request 0 [ SA V V V V V ]
Jun 8 00:59:20 r1-roll charon: 07[NET] <peer-192.0.2.2-tunnel-0|1> sending packet: from 192.0.2.1[500] to 192.0.2.2[500] (180 bytes)
Jun 8 00:59:20 r1-roll charon: 09[NET] <peer-192.0.2.2-tunnel-0|1> received packet: from 192.0.2.2[500] to 192.0.2.1[500] (160 bytes)
Jun 8 00:59:20 r1-roll charon: 09[ENC] <peer-192.0.2.2-tunnel-0|1> parsed ID_PROT response 0 [ SA V V V V ]
Jun 8 00:59:20 r1-roll charon: 09[IKE] <peer-192.0.2.2-tunnel-0|1> received XAuth vendor ID
Jun 8 00:59:20 r1-roll charon: 09[IKE] <peer-192.0.2.2-tunnel-0|1> received DPD vendor ID
Jun 8 00:59:20 r1-roll charon: 09[IKE] <peer-192.0.2.2-tunnel-0|1> received FRAGMENTATION vendor ID
Jun 8 00:59:20 r1-roll charon: 09[IKE] <peer-192.0.2.2-tunnel-0|1> received NAT-T (RFC 3947) vendor ID
Jun 8 00:59:20 r1-roll charon: 09[CFG] <peer-192.0.2.2-tunnel-0|1> selected proposal: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Jun 8 00:59:20 r1-roll charon: 09[ENC] <peer-192.0.2.2-tunnel-0|1> generating ID_PROT request 0 [ KE No NAT-D NAT-D ]
Jun 8 00:59:20 r1-roll charon: 09[NET] <peer-192.0.2.2-tunnel-0|1> sending packet: from 192.0.2.1[500] to 192.0.2.2[500] (244 bytes)
Jun 8 00:59:20 r1-roll charon: 10[NET] <peer-192.0.2.2-tunnel-0|1> received packet: from 192.0.2.2[500] to 192.0.2.1[500] (244 bytes)
Jun 8 00:59:20 r1-roll charon: 10[ENC] <peer-192.0.2.2-tunnel-0|1> parsed ID_PROT response 0 [ KE No NAT-D NAT-D ]
Jun 8 00:59:20 r1-roll charon: 10[ENC] <peer-192.0.2.2-tunnel-0|1> generating ID_PROT request 0 [ ID HASH N(INITIAL_CONTACT) ]
Jun 8 00:59:20 r1-roll charon: 10[NET] <peer-192.0.2.2-tunnel-0|1> sending packet: from 192.0.2.1[500] to 192.0.2.2[500] (108 bytes)
Jun 8 00:59:20 r1-roll charon: 11[NET] <peer-192.0.2.2-tunnel-0|1> received packet: from 192.0.2.2[500] to 192.0.2.1[500] (76 bytes)
Jun 8 00:59:20 r1-roll charon: 11[ENC] <peer-192.0.2.2-tunnel-0|1> parsed ID_PROT response 0 [ ID HASH ]
Jun 8 00:59:20 r1-roll charon: 11[IKE] <peer-192.0.2.2-tunnel-0|1> IKE_SA peer-192.0.2.2-tunnel-0[1] established between 192.0.2.1[192.0.2.1]...192.0.2.2[192.0.2.2]
Jun 8 00:59:20 r1-roll charon: 11[IKE] <peer-192.0.2.2-tunnel-0|1> scheduling rekeying in 2720s
Jun 8 00:59:20 r1-roll charon: 11[IKE] <peer-192.0.2.2-tunnel-0|1> maximum IKE_SA lifetime 3260s
Jun 8 00:59:20 r1-roll charon: 11[ENC] <peer-192.0.2.2-tunnel-0|1> generating QUICK_MODE request 3783917425 [ HASH SA No KE ID ID ]
Jun 8 00:59:20 r1-roll charon: 11[NET] <peer-192.0.2.2-tunnel-0|1> sending packet: from 192.0.2.1[500] to 192.0.2.2[500] (316 bytes)
Jun 8 00:59:20 r1-roll charon: 12[NET] <peer-192.0.2.2-tunnel-0|1> received packet: from 192.0.2.2[500] to 192.0.2.1[500] (316 bytes)
Jun 8 00:59:20 r1-roll charon: 12[ENC] <peer-192.0.2.2-tunnel-0|1> parsed QUICK_MODE response 3783917425 [ HASH SA No KE ID ID ]
Jun 8 00:59:20 r1-roll charon: 12[CFG] <peer-192.0.2.2-tunnel-0|1> selected proposal: ESP:AES_CBC_256/HMAC_SHA1_96/MODP_1024/NO_EXT_SEQ
Jun 8 00:59:20 r1-roll charon: 12[IKE] <peer-192.0.2.2-tunnel-0|1> CHILD_SA peer-192.0.2.2-tunnel-0{1} established with SPIs c4d940b7_i c9a69e83_o and TS 10.1.0.0/24 === 10.2.3.0/24
Jun 8 00:59:20 r1-roll charon: 12[ENC] <peer-192.0.2.2-tunnel-0|1> generating QUICK_MODE request 3783917425 [ HASH ]
Jun 8 00:59:20 r1-roll charon: 12[NET] <peer-192.0.2.2-tunnel-0|1> sending packet: from 192.0.2.1[500] to 192.0.2.2[500] (60 bytes)@arvin This functions in all versions of VyOS.
I can't reproduce it in 1.2.7 and VyOS 1.3-beta-202105272051
@jingyun Can you describe steps on how to reproduce it? Or re-check it.
My test config after reboot works fine
set interfaces bridge br0 member interface tun0 set interfaces tunnel tun0 encapsulation 'gre-bridge' set interfaces tunnel tun0 local-ip '100.64.0.1' set interfaces tunnel tun0 remote-ip '100.64.0.254'
In the crux.
set system conntrack timeout custom rule 10 destination address '203.0.113.74' set system conntrack timeout custom rule 10 destination port '80' set system conntrack timeout custom rule 10 protocol tcp established '300' set system conntrack timeout custom rule 10 source address '192.0.2.168'
commit
vyos@r2-lts# commit [ system conntrack hash-size 32768 ] Updated conntrack hash size. This change will take affect when the system is rebooted.
Jun 2 2021
It seems after that commit
but it is not a root case
Jun 1 2021
Note
ipsec-interface not deprecated. This option needed.
set vpn ipsec ipsec-interfaces interface 'eth1'
set vpn ipsec esp-group ESP-GRP compression 'disable' set vpn ipsec esp-group ESP-GRP lifetime '1800' set vpn ipsec esp-group ESP-GRP mode 'tunnel' set vpn ipsec esp-group ESP-GRP pfs 'enable' set vpn ipsec esp-group ESP-GRP proposal 1 encryption 'aes256' set vpn ipsec esp-group ESP-GRP proposal 1 hash 'sha1' set vpn ipsec ike-group IKE-GRP ikev2-reauth 'no' set vpn ipsec ike-group IKE-GRP key-exchange 'ikev1' set vpn ipsec ike-group IKE-GRP lifetime '3600' set vpn ipsec ike-group IKE-GRP proposal 1 encryption 'aes256' set vpn ipsec ike-group IKE-GRP proposal 1 hash 'sha1' set vpn ipsec ipsec-interfaces interface 'eth1' set vpn ipsec site-to-site peer c01d:c01a:cafe::1 authentication mode 'pre-shared-secret' set vpn ipsec site-to-site peer c01d:c01a:cafe::1 authentication pre-shared-secret 'SeCrEt' set vpn ipsec site-to-site peer c01d:c01a:cafe::1 connection-type 'respond' set vpn ipsec site-to-site peer c01d:c01a:cafe::1 ike-group 'IKE-GRP' set vpn ipsec site-to-site peer c01d:c01a:cafe::1 local-address 'c01d:c01a:cafe::2' set vpn ipsec site-to-site peer c01d:c01a:cafe::1 tunnel 0 allow-nat-networks 'disable' set vpn ipsec site-to-site peer c01d:c01a:cafe::1 tunnel 0 allow-public-networks 'disable' set vpn ipsec site-to-site peer c01d:c01a:cafe::1 tunnel 0 esp-group 'ESP-GRP' set vpn ipsec site-to-site peer c01d:c01a:cafe::1 tunnel 0 local prefix '2001:db7::/64' set vpn ipsec site-to-site peer c01d:c01a:cafe::1 tunnel 0 remote prefix '2001:db8::/64' set vpn ipsec site-to-site peer c01d:c01a:cafe::1 tunnel 1 allow-nat-networks 'disable' set vpn ipsec site-to-site peer c01d:c01a:cafe::1 tunnel 1 allow-public-networks 'disable' set vpn ipsec site-to-site peer c01d:c01a:cafe::1 tunnel 1 esp-group 'ESP-GRP' set vpn ipsec site-to-site peer c01d:c01a:cafe::1 tunnel 1 local prefix '10.2.3.0/24' set vpn ipsec site-to-site peer c01d:c01a:cafe::1 tunnel 1 remote prefix '10.1.0.0/24'
May 31 2021
@mTx87 Do you have a working example in Linux?
Maybe it also needs OpenVPN >= 2.5.0
https://blog.sdn.clinic/2018/12/openvpn-and-vrfs/
May 29 2021
root@r2-lts:/home/vyos# snmpget -v 2c -c public 192.168.122.11 IF-MIB::ifAdminStatus.1 IF-MIB::ifAdminStatus.1 = INTEGER: up(1)
May 27 2021
The reason it such script https://github.com/vyos/vyatta-cfg-quagga/blob/d962ef0f2c15333411e719f7d1b02dd7575ebdee/scripts/bgp/vyatta-bgp.pl#L385
That do
router bgp xxx address-family ipv4 unicast no neighbor x.x.x.x activate
May 26 2021
FRR doing normalization for ipv6
Possible was fixed in that task T3502
Unfortunately, I can't reproduce it.
Also, all smoke test for static routes looks good.
vyos@r4-1.3# set protocols static route 192.0.2.0/24 dhcp-interface Possible completions: <text> DHCP interface name eth0 eth1 lo
@olofl Add please a separate task for JSON.
As I understand the needed section
[pppd-compat] verbose=1 #ip-pre-up=/etc/ppp/ip-pre-up ip-up=/etc/ppp/ip-up ip-down=/etc/ppp/ip-down #ip-change=/etc/ppp/ip-change radattr-prefix=/var/run/radattr #fork-limit=16