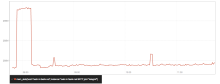
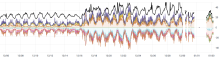
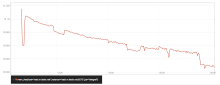
We've been having a similar issue as to what is reported here.
https://sourceforge.net/p/e1000/mailman/e1000-devel/?viewmonth=202012
Vyos 1.3-rolling is still using the out of tree drivers for Intel network cards.
Now the kernel has moved to 5.4 series is it worth switching to the in-kernel drivers?
Is there anything that the out-of-kernel driver supports that kernel 5.4 doesn't?
The latest 5.4. kernel looks like it might have a fix just released for our problem.
The OP at sourceforge indicated that the in-kernel driver has resolved it for them.