As discussed in the maintainer's slack channel will be good to replace CLI commands from set vpn anyconnect to set vpn openconnect. But in our docs we should use anyconnect-compatible server.
- Feed Queries
- All Stories
- Search
- Feed Search
- Transactions
- Transaction Logs
Sep 9 2020
Sep 8 2020
PR from @ronie https://github.com/vyos/vyos-documentation/pull/317
Sep 7 2020
Intel QAT works for CRUX brunch. As for rolling with the newest kernel 5.8.5, it seems some issues on the modules building stage.
Sep 6 2020
@c-po I build qat manually but add --enable-qat-lkcf to https://github.com/vyos/vyos-build/blob/crux/packages/linux-kernel/build-intel-qat.sh#L55 and it seems it works
vyos@R2-QAT:~$ show system acceleration qat device qat_dev0 flows +------------------------------------------------+ | FW Statistics for Qat Device | +------------------------------------------------+ | Firmware Requests [AE 0]: 147225 | | Firmware Responses[AE 0]: 147225 | +------------------------------------------------+ | Firmware Requests [AE 1]: 113758 | | Firmware Responses[AE 1]: 113758 | +------------------------------------------------+ | Firmware Requests [AE 2]: 144886 | | Firmware Responses[AE 2]: 144886 | +------------------------------------------------+ | Firmware Requests [AE 3]: 147221 | | Firmware Responses[AE 3]: 147221 | +------------------------------------------------+ | Firmware Requests [AE 4]: 113774 | | Firmware Responses[AE 4]: 113774 | +------------------------------------------------+ | Firmware Requests [AE 5]: 144891 | | Firmware Responses[AE 5]: 144891 | +------------------------------------------------+
Tested on 1.3-rolling-202009060846
Sep 3 2020
Sep 2 2020
Sep 1 2020
@maznu but it seems really odd behavior, I mean message settled in 121 sec. failed!
121 sec - equal to 121 interfaces when the router is first booted. But if in config already present hw-id, it should be faster then 0 sec.
Will be interesting to reproduce this in our lab. Also will be helpful if you provide sudo dmesg output.
Aug 31 2020
Hello @marekm, I think [ppp]unit-cache=n might help in this case, but the main issue in FRR. Do you want a package for the test with these improvements?
unit-cache=n By default is disabled: unit-cache=0
Aug 30 2020
I tested this in LAB and it seems works properly. Changing interface name for eth1 and eth2
vyos@vyos# delete interfaces ethernet eth1 hw-id [edit] vyos@vyos# delete interfaces ethernet eth2 hw-id [edit] vyos@vyos# set interfaces ethernet eth1 hw-id 50:01:00:02:00:02 [edit] vyos@vyos# set interfaces ethernet eth2 hw-id 50:01:00:02:00:01 [edit] vyos@vyos# commit [edit] vyos@vyos# save Saving configuration to '/config/config.boot'... Done [edit] vyos@vyos# run reboot now
After reboot
vyos@vyos:~$ sudo ethtool -P eth1 Permanent address: 50:01:00:02:00:02 vyos@vyos:~$ sudo ethtool -P eth2 Permanent address: 50:01:00:02:00:01
@maznu , can you provide next:
show configuration commands | match hw-id sudo cat /run/udev/log/vyatta-net-name.coldplug
Aug 27 2020
Aug 26 2020
Aug 23 2020
Jenkins output build ID 1015
16:14:06 DEBUG - Running Testcase: /usr/libexec/vyos/tests/smoke/cli/test_vpn_anyconnect.py 16:14:18 DEBUG - . 16:14:18 DEBUG - ---------------------------------------------------------------------- 16:14:18 DEBUG - Ran 1 test in 11.085s 16:14:18 DEBUG - 16:14:18 DEBUG - OK
Works properly, tested on 1.3-rolling-202008231246
Aug 20 2020
Aug 19 2020
This happens only when in config before migration exists nodes system 'ntp' without other params.
Works as expected on VyOS 1.3-rolling-202008190118
Aug 18 2020
Aug 14 2020
Successfully tested on VyOS 1.2.6-epa1
Aug 13 2020
Hi @dongjunbo , could you try the package for 1.2.5 with fixing this issue?
Aug 12 2020
Aug 3 2020
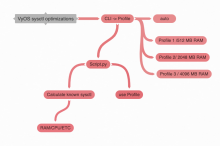
The main idea to add some automation logic for calculation:
vyos@vyos# set system sysctl profile Possible completions: <text> Sysctl profile Profile1 Profile2 auto
Hi @jack9603301 , in normal condition all scripts and files should be migrated from /config/ directory on the migration process.
Jul 30 2020
Jul 24 2020
Jul 10 2020
Jul 5 2020
Necessary run service with priority for correct starting https://github.com/vyos/vyos-1x/pull/489
Jul 3 2020
PR https://github.com/vyos/vyos-1x/pull/487 with changed CLI to service ids ddos-protection.
Jun 29 2020
Jun 27 2020
Yes, it is possible not only to detect DoS/DDoS and also to make some reactions and run alert script.
Alert script receives next params:
# $1 client_ip_as_string # $2 data_direction # $3 pps_as_string # $4 action (ban or unban)
@jack9603301 can you explain snort perspectives and describe the difference between? Do you have experience with both IDS?
Jun 24 2020
Jun 22 2020
Jun 21 2020
Works as expected, tested on 1.3-rolling-202006201113
Jun 20 2020
Jun 18 2020
Can I propose this do as default but keep the possibility redefine replace option?
Jun 17 2020
@c-po Yes, sorry. This is my fault, I forgot that you told me already this.
Done, PR https://github.com/vyos/vyos-1x/pull/464
Add PR for rolling https://github.com/vyos/vyos-1x/pull/462
Jun 16 2020
Implementation steps:
- Add $INCLUDE dictionary.rfc4849 to /usr/share/accel-ppp/radius/dictionary file
- Add required modules for use ip-pre-up/ip-up/ip-down scripts
[modules] sigchld pppd_compat
And pppd_compat params
[pppd-compat] verbose=1 ip-pre-up=/path/to/ip-pre-up radattr-prefix=/var/run/radattr
- Create ip-pre-up/ip-down script which will get configured firewall names and rules from CLI or supported script
Note: When ip-pre-up return 1 then the session will not start like described in https://tools.ietf.org/html/rfc4849
Does not possible to disable ccp in l2tp
vyos@RTR1# set vpn l2tp remote-access ccp-disable [edit] vyos@RTR1# commit [ vpn l2tp ] VyOS had an issue completing a command.
Jun 15 2020
I think this is a related task https://phabricator.vyos.net/T2591
Jun 14 2020
Jun 13 2020
Jun 12 2020
Successfully tested on 1.3-rolling-202006120643
Successfully tested on rolling 1.3-rolling-202006120643
Jun 11 2020
Jun 10 2020
ipoe daemon allows us to use this possibility. We need to add CLI commands.
Proposed commands:
set service ipoe-server client-ip-pool name POOL1 subnet 100.64.0.0/24
Radius attribute Framed-Pool.
Tested on VyOS 1.3-rolling-202006101523
SSTP, L2TP and PPPoE work as expected.
As for pptp, needs to create an additional bug report
Jun 9 2020
In this case, SSTP daemon trying to allocate RAM for ipv6 pool and router does not have enough RAM. Dynamic memory allocation is not implemented for ip-pools.
Maybe, in this case, we need to calculate before commit, and show commit fail message with reason?
Calculating:
2^64 bit = 18446744073709551616 bit or 2305843009213693952 byte
2305843009213693952 * 64 (structure size byte) = 147573952589676412928 byte or 137438953472 GB
Correct me if my calculation wrong.
Jun 8 2020
PR https://github.com/vyos/vyos-1x/pull/446
Note: gw-ip-address necessary define for [radius] or [chap-secrets] sections.
@c-po these changes will take effect only for the newly installed system, HW-ID in config has more priority.