@zsdc can you try to reproduce this issue on 1.3 rollings or on 1.2.5? I can't reach this behavior.
- Feed Queries
- All Stories
- Search
- Feed Search
- Transactions
- Transaction Logs
Jun 7 2020
May 29 2020
May 28 2020
PR added https://github.com/vyos/vyatta-cfg-vpn/pull/33.
vyos@vyos# commit [ vpn ] Warning: local prefix 192.168.34.0/24 specified for peer "192.168.50.2" is not configured on any interfaces
PR https://github.com/vyos/vyatta-cfg-quagga/pull/48
Also added the second commit which fixes the path to zebra daemon
May 26 2020
Successfully tested on 1.3-rolling-202005261512, propose to backport it to CRUX.
May 25 2020
Hello @lawrencepan , can you explain, why you need different AS for route-reflector-client?
Can you add your route-maps ROUTE-V4 and 'ROUTER-V6?
PR for this task https://github.com/vyos/libpam-radius-auth/pull/3
I propose to use always source-address as NAS-IP-Address if it defined
Tested successfully on 1.3-rolling-202005250117
vyos@RTR1:~$ show sstp-server sessions ifname | username | ip | ip6 | ip6-dp | calling-sid | rate-limit | state | uptime | rx-bytes | tx-bytes --------+----------+------------+-----+--------+-------------+------------+--------+----------+----------+---------- sstp0 | test | 100.64.2.0 | | | x.x.x.x. | | active | 00:01:16 | 27.9 KiB | 80.3 KiB
Tested on 1.3-rolling-202005250117, works as expected.
May 22 2020
Maybe set service serial-bridge?
May 21 2020
Tested on 1.3-rolling-202005210117, works properly
May 20 2020
Note: When we migrate NAT to nftables, we need to use nftables sets instead of ipset
May 19 2020
May 14 2020
May 13 2020
Issue with socket.gethostbyname()
Successfully tested on the VyOS 1.3-rolling-202005130117.
Full opennhrp logs might be enabled by the following command
Fixed in T832
May 11 2020
May 9 2020
May 6 2020
May 4 2020
Fix path to mac-address node. PR https://github.com/vyos/vyos-1x/pull/392
All works on the rolling 1.3-rolling-202005030117
vyos@vyos:~$ ping 100.64.0.1 flood count 300 PING 100.64.0.1 (100.64.0.1) 56(84) bytes of data.
May 2 2020
May 1 2020
Apr 28 2020
Apr 27 2020
Successfully tested on 1.3-rolling-202004270117
Apr 26 2020
Phabricator didn't get patches without task number, but this already in rolling
https://github.com/vyos/vyatta-op/commit/8dd886c9542cefe09d5a722307e0acbbf41ee9b8
I propose to backport this into crux.
Apr 23 2020
PR https://github.com/vyos/vyos-1x/pull/374
Possible commands:
vyos@R1-VM# set service pppoe-server authentication protocols Possible completions: pap Allow PAP authentication [Password Authentication Protocol] chap Allow CHAP authentication [Challenge Handshake Authentication Protocol] mschap Allow MS-CHAP authentication [Microsoft Challenge Handshake Authentication Protocol, Version 1] mschap-v2 Allow MS-CHAPv2 authentication [Microsoft Challenge Handshake Authentication Protocol, Version 2]
Apr 21 2020
Make sense, because IPIP this is L3, the bridge is L2.
In this case, we should not show L3 as an allowed interface for bridge.
crux has another syntax, but interface tunnels not bridgeable in crux
With this patch, all works as expected. Thanks @thomas-mangin
Related with https://phabricator.vyos.net/T2223
Apr 20 2020
PR https://github.com/vyos/vyatta-cfg-system/pull/123
@Viacheslav can you double-check this package with most popular interfaces in the bridge?
Apr 18 2020
PR for this task https://github.com/vyos/vyos-1x/pull/354
Apr 17 2020
@Viacheslav can you check?
Apr 16 2020
PR for other servers https://github.com/vyos/vyos-1x/pull/350
I can confirm this bug, also exist in 1.2.5 OVA
Is 1.2.3 was deployed from OVA or install from ISO?
Which hypervisor?
Apr 15 2020
PR for fixing this issue https://github.com/vyos/vyos-1x/pull/347
After drawing some use cases I will propose to modify auth schema by LUA
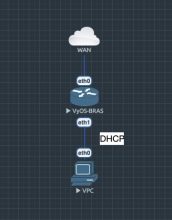
@c-po this is just DHCP-client in this case, Windows, Linux or VPC (Virtual PC).
Apr 14 2020
Improve op-mode commands for ipoe-server
https://github.com/vyos/vyos-1x/pull/344
vyos@vyos:~$ show ipoe-server sessions ifname | username | calling-sid | ip | rate-limit | type | comp | state | uptime --------+----------+-------------------+------------+------------+------+------+--------+---------- ipoe0 | | 00:50:79:66:68:09 | 100.64.0.2 | | ipoe | | active | 00:00:11 ipoe1 | | 00:50:79:66:68:0a | 100.64.0.3 | | ipoe | | active | 00:00:09
Apr 13 2020
Note: will be good to disable this by udev rule for i40e
Apr 12 2020
Tested on 1.2.5