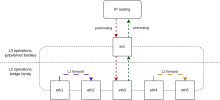
Minimal configuration:
set interfaces bridge br0 enable-vlan set interfaces bridge br0 ip adjust-mss '1377' set interfaces bridge br0 member interface eth0 allowed-vlan '2' set interfaces bridge br0 member interface eth1 allowed-vlan '2'
On connections passing through the router, mss is not changed:
vyos@br:~$ sudo tcpdump -ni any tcp and port 22 tcpdump: data link type LINUX_SLL2 tcpdump: verbose output suppressed, use -v[v]... for full protocol decode listening on any, link-type LINUX_SLL2 (Linux cooked v2), snapshot length 262144 bytes 19:57:26.972589 eth1 P IP 10.2.2.33.58870 > 10.2.2.22.22: Flags [S], seq 2012243087, win 32120, options [mss 1460,sackOK,TS val 4271284820 ecr 0,nop,wscale 7], length 0 19:57:26.972623 eth0 Out IP 10.2.2.33.58870 > 10.2.2.22.22: Flags [S], seq 2012243087, win 32120, options [mss 1460,sackOK,TS val 4271284820 ecr 0,nop,wscale 7], length 0
Adding rules at bridge level using custom nft rules do the trick:
sudo nft add table bridge vyos_filter
sudo nft add chain bridge vyos_filter bridge_prerouting { type filter hook prerouting priority -200 \; }
sudo nft add rule bridge vyos_filter bridge_prerouting tcp flags syn counter tcp option maxseg size set 1355And tcpdump:
vyos@br# sudo tcpdump -ni any tcp and port 22 tcpdump: data link type LINUX_SLL2 tcpdump: verbose output suppressed, use -v[v]... for full protocol decode listening on any, link-type LINUX_SLL2 (Linux cooked v2), snapshot length 262144 bytes 20:06:22.693778 eth1 P IP 10.2.2.33.53818 > 10.2.2.22.22: Flags [S], seq 3036941485, win 32120, options [mss 1460,sackOK,TS val 4271820541 ecr 0,nop,wscale 7], length 0 20:06:22.693921 eth0 Out IP 10.2.2.33.53818 > 10.2.2.22.22: Flags [S], seq 3036941485, win 32120, options [mss 1355,sackOK,TS val 4271820541 ecr 0,nop,wscale 7], length 0