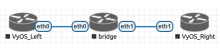
Currently, VyOS in bridge mode cannot filter traffic on interfaces in bridge mode
The basic idea is to use "table bridge filter" instead of "table ip filter". Maybe there are other ways.
Such functionality would be extremely useful in some scenarios.
Also, this support is desirable for VLAN subinterfaces
Traffic is not filtered at the moment:
set interfaces ethernet eth0 vif 705
set interfaces ethernet eth1 vif 706
set interfaces bridge br1 member interface eth0.705
set interfaces bridge br1 member interface eth1.706
set firewall name access_in rule 10 action 'drop'
set firewall name access_in rule 10 protocol 'ip'
set firewall name access_in rule 10 source address 0.0.0.0/0
set firewall name access_in rule 10 destination address 0.0.0.0/0
set interfaces ethernet eth1 vif 706 firewall in name 'access_in '
set interfaces ethernet eth0 vif 705 firewall in name 'access_in '