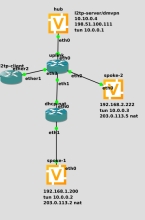
Dmvpn works until we do not configure the l2tp server
Hub configuration:
set interfaces dummy dum0 address '198.51.100.111/32' set interfaces ethernet eth0 address 'dhcp' set interfaces tunnel tun0 address '10.0.0.1/24' set interfaces tunnel tun0 encapsulation 'gre' set interfaces tunnel tun0 local-ip '198.51.100.111' set interfaces tunnel tun0 multicast 'enable' set interfaces tunnel tun0 parameters ip key '1' set nat destination rule 20 inbound-interface 'eth0' set nat destination rule 20 translation address '198.51.100.111' set protocols nhrp tunnel tun0 cisco-authentication '12345' set protocols nhrp tunnel tun0 holding-time '300' set protocols nhrp tunnel tun0 multicast 'dynamic' set protocols nhrp tunnel tun0 redirect set system host-name 'r1-hub' set vpn ipsec esp-group ESP-HUB compression 'disable' set vpn ipsec esp-group ESP-HUB lifetime '1800' set vpn ipsec esp-group ESP-HUB mode 'transport' set vpn ipsec esp-group ESP-HUB pfs 'dh-group2' set vpn ipsec esp-group ESP-HUB proposal 1 encryption 'aes256' set vpn ipsec esp-group ESP-HUB proposal 1 hash 'sha1' set vpn ipsec esp-group ESP-HUB proposal 2 encryption '3des' set vpn ipsec esp-group ESP-HUB proposal 2 hash 'md5' set vpn ipsec ike-group IKE-HUB close-action 'none' set vpn ipsec ike-group IKE-HUB ikev2-reauth 'no' set vpn ipsec ike-group IKE-HUB key-exchange 'ikev1' set vpn ipsec ike-group IKE-HUB lifetime '3600' set vpn ipsec ike-group IKE-HUB proposal 1 dh-group '2' set vpn ipsec ike-group IKE-HUB proposal 1 encryption 'aes256' set vpn ipsec ike-group IKE-HUB proposal 1 hash 'sha1' set vpn ipsec ike-group IKE-HUB proposal 2 dh-group '2' set vpn ipsec ike-group IKE-HUB proposal 2 encryption 'aes128' set vpn ipsec ike-group IKE-HUB proposal 2 hash 'sha1' set vpn ipsec ipsec-interfaces interface 'dum0' set vpn ipsec nat-networks allowed-network 0.0.0.0/0 set vpn ipsec nat-traversal 'enable' set vpn ipsec profile NHRPVPN authentication mode 'pre-shared-secret' set vpn ipsec profile NHRPVPN authentication pre-shared-secret 'SeCret' set vpn ipsec profile NHRPVPN bind tunnel 'tun0' set vpn ipsec profile NHRPVPN esp-group 'ESP-HUB' set vpn ipsec profile NHRPVPN ike-group 'IKE-HUB' ### Additional l2tp server configuration set vpn ipsec nat-networks allowed-network 0.0.0.0/0 set vpn ipsec nat-traversal 'enable' set vpn l2tp remote-access authentication local-users username foo password bar set vpn l2tp remote-access authentication mode 'local' set vpn l2tp remote-access authentication require 'chap' set vpn l2tp remote-access client-ip-pool start 10.20.30.10 set vpn l2tp remote-access client-ip-pool stop 10.20.30.50 set vpn l2tp remote-access description 'VPN-REMOTE' set vpn l2tp remote-access dns-servers server-1 '1.1.1.1' set vpn l2tp remote-access idle '1800' set vpn l2tp remote-access ipsec-settings authentication mode 'pre-shared-secret' set vpn l2tp remote-access ipsec-settings authentication pre-shared-secret 'PasSw' set vpn l2tp remote-access ipsec-settings ike-lifetime '8600' set vpn l2tp remote-access ipsec-settings lifetime '3600' set vpn l2tp remote-access outside-address '198.51.100.111'
Spoke configuration:
set interfaces ethernet eth0 address 'dhcp' set interfaces tunnel tun0 address '10.0.0.2/24' set interfaces tunnel tun0 encapsulation 'gre' set interfaces tunnel tun0 local-ip '0.0.0.0' set interfaces tunnel tun0 multicast 'enable' set interfaces tunnel tun0 parameters ip key '1' set protocols nhrp tunnel tun0 cisco-authentication '12345' set protocols nhrp tunnel tun0 map 10.0.0.1/24 nbma-address '198.51.100.111' set protocols nhrp tunnel tun0 map 10.0.0.1/24 register set protocols nhrp tunnel tun0 multicast 'nhs' set protocols nhrp tunnel tun0 redirect set protocols nhrp tunnel tun0 shortcut set system host-name 'spoke-1' set vpn ipsec esp-group ESP-SPOKE compression 'disable' set vpn ipsec esp-group ESP-SPOKE lifetime '1800' set vpn ipsec esp-group ESP-SPOKE mode 'transport' set vpn ipsec esp-group ESP-SPOKE pfs 'dh-group2' set vpn ipsec esp-group ESP-SPOKE proposal 1 encryption 'aes256' set vpn ipsec esp-group ESP-SPOKE proposal 1 hash 'sha1' set vpn ipsec esp-group ESP-SPOKE proposal 2 encryption '3des' set vpn ipsec esp-group ESP-SPOKE proposal 2 hash 'md5' set vpn ipsec ike-group IKE-SPOKE close-action 'none' set vpn ipsec ike-group IKE-SPOKE ikev2-reauth 'no' set vpn ipsec ike-group IKE-SPOKE key-exchange 'ikev1' set vpn ipsec ike-group IKE-SPOKE lifetime '3600' set vpn ipsec ike-group IKE-SPOKE proposal 1 dh-group '2' set vpn ipsec ike-group IKE-SPOKE proposal 1 encryption 'aes256' set vpn ipsec ike-group IKE-SPOKE proposal 1 hash 'sha1' set vpn ipsec ike-group IKE-SPOKE proposal 2 dh-group '2' set vpn ipsec ike-group IKE-SPOKE proposal 2 encryption 'aes128' set vpn ipsec ike-group IKE-SPOKE proposal 2 hash 'sha1' set vpn ipsec ipsec-interfaces interface 'eth0' set vpn ipsec profile NHRPVPN authentication mode 'pre-shared-secret' set vpn ipsec profile NHRPVPN authentication pre-shared-secret 'SeCret' set vpn ipsec profile NHRPVPN bind tunnel 'tun0' set vpn ipsec profile NHRPVPN esp-group 'ESP-SPOKE' set vpn ipsec profile NHRPVPN ike-group 'IKE-SPOKE'
Without l2tp configuration all works fine. Tunnels up and spoke1 can ping spoke2
Sep 21 09:25:24 r1-hub charon: 07[NET] <dmvpn-NHRPVPN-tun0|1> received packet: from 203.0.113.2[4500] to 198.51.100.111[4500] (60 bytes)
Sep 21 09:25:24 r1-hub charon: 07[ENC] <dmvpn-NHRPVPN-tun0|1> parsed QUICK_MODE request 1167445042 [ HASH ]
Sep 21 09:25:24 r1-hub charon: 08[NET] <dmvpn-NHRPVPN-tun0|2> received packet: from 203.0.113.5[4500] to 198.51.100.111[4500] (60 bytes)
Sep 21 09:25:24 r1-hub charon: 08[ENC] <dmvpn-NHRPVPN-tun0|2> parsed QUICK_MODE request 3792048823 [ HASH ]
Sep 21 09:25:24 r1-hub charon: 07[IKE] <dmvpn-NHRPVPN-tun0|1> CHILD_SA dmvpn{1} established with SPIs cc286b77_i c3efa53c_o and TS 198.51.100.111/32[gre] === 203.0.113.2/32[gre]
Sep 21 09:25:24 r1-hub charon: 08[IKE] <dmvpn-NHRPVPN-tun0|2> CHILD_SA dmvpn{2} established with SPIs cf212943_i c9db0e9a_o and TS 198.51.100.111/32[gre] === 203.0.113.5/32[gre]
Sep 21 09:46:42 r1-hub opennhrp[2049]: Sending Traffic Indication about packet from 10.0.0.2 to 10.0.0.3 (to 10.0.0.2/203.0.113.2)
Sep 21 09:46:42 r1-hub opennhrp[2049]: Sending packet 8, from: 10.0.0.1 (nbma 198.51.100.111), to: 10.0.0.2 (nbma 203.0.113.2)
Sep 21 09:46:42 r1-hub opennhrp[2049]: Forwarding packet from nbma src 192.168.2.222, proto src 10.0.0.3 to proto dst 10.0.0.2, hop count 16
Sep 21 09:46:42 r1-hub opennhrp[2049]: Sending packet 1, from: 10.0.0.3 (nbma 192.168.2.222), to: 10.0.0.2 (nbma 203.0.113.2)
Sep 21 09:46:42 r1-hub opennhrp[2049]: Sending Traffic Indication about packet from 10.0.0.3 to 10.0.0.2 (to 10.0.0.3/203.0.113.5)
Sep 21 09:46:42 r1-hub opennhrp[2049]: Sending packet 8, from: 10.0.0.1 (nbma 198.51.100.111), to: 10.0.0.3 (nbma 203.0.113.5)
Sep 21 09:46:42 r1-hub opennhrp[2049]: Forwarding packet from nbma src 192.168.2.222, proto src 10.0.0.3 to proto dst 10.0.0.2, hop count 16
Sep 21 09:46:42 r1-hub opennhrp[2049]: Sending packet 2, from: 10.0.0.3 (nbma 192.168.2.222), to: 10.0.0.2 (nbma 203.0.113.5)
Sep 21 09:46:47 r1-hub opennhrp[2049]: Forwarding packet from nbma src 192.168.1.200, proto src 10.0.0.2 to proto dst 10.0.0.3, hop count 16
Sep 21 09:46:47 r1-hub opennhrp[2049]: Sending packet 1, from: 10.0.0.2 (nbma 192.168.1.200), to: 10.0.0.3 (nbma 203.0.113.5)
Sep 21 09:46:47 r1-hub opennhrp[2049]: Sending Traffic Indication about packet from 10.0.0.2 to 10.0.0.3 (to 10.0.0.2/203.0.113.2)
Sep 21 09:46:47 r1-hub opennhrp[2049]: Sending packet 8, from: 10.0.0.1 (nbma 198.51.100.111), to: 10.0.0.2 (nbma 203.0.113.2)
Sep 21 09:46:47 r1-hub opennhrp[2049]: Forwarding packet from nbma src 192.168.1.200, proto src 10.0.0.2 to proto dst 10.0.0.3, hop count 16
Sep 21 09:46:47 r1-hub opennhrp[2049]: Sending packet 2, from: 10.0.0.2 (nbma 192.168.1.200), to: 10.0.0.3 (nbma 203.0.113.2)
Sep 21 09:46:47 r1-hub opennhrp[2049]: NL-ARP(tun0) who-has 10.0.0.2
Sep 21 09:46:47 r1-hub opennhrp[2049]: NL-ARP(tun0) 10.0.0.2 is-at 203.0.113.2
Sep 21 09:46:47 r1-hub opennhrp[2049]: NL-ARP(tun0) who-has 10.0.0.3
Sep 21 09:46:47 r1-hub opennhrp[2049]: NL-ARP(tun0) 10.0.0.3 is-at 203.0.113.5After adding l2tp configuration on the hub we need reset nhrp on the spoke1
vyos@spoke-1:~$ reset nhrp flush tunnel Status: ok Entries-Affected: 1 vyos@spoke-1:~$
Logs from hub:
Sep 21 09:51:59 r1-hub opennhrp[2842]: NL-ARP(tun0) who-has 10.0.0.3 Sep 21 09:52:00 r1-hub opennhrp[2842]: NL-ARP(tun0) who-has 10.0.0.3 Sep 21 09:52:01 r1-hub opennhrp[2842]: Forwarding packet from nbma src 192.168.1.200, proto src 10.0.0.2 to proto dst 10.0.0.3, hop count 16 Sep 21 09:52:01 r1-hub opennhrp[2842]: No peer entry for protocol address 10.0.0.3 Sep 21 09:52:01 r1-hub opennhrp[2842]: No peer entry for protocol address 10.0.0.2 Sep 21 09:52:01 r1-hub opennhrp[2842]: NL-ARP(tun0) who-has 10.0.0.2 Sep 21 09:52:01 r1-hub opennhrp[2842]: NL-ARP(tun0) who-has 10.0.0.3 Sep 21 09:52:02 r1-hub opennhrp[2842]: NL-ARP(tun0) who-has 10.0.0.3
Save configuration and reboot hub (to update all old keys)
Logs from hub:
Sep 21 09:54:14 r1-hub xl2tpd[2060]: Listening on IP address 198.51.100.111, port 1701 Sep 21 09:54:31 r1-hub charon: 08[NET] <1> received packet: from 203.0.113.2[500] to 198.51.100.111[500] (216 bytes) Sep 21 09:54:31 r1-hub charon: 08[ENC] <1> parsed ID_PROT request 0 [ SA V V V V V ] Sep 21 09:54:31 r1-hub charon: 08[IKE] <1> received XAuth vendor ID Sep 21 09:54:31 r1-hub charon: 08[IKE] <1> received DPD vendor ID Sep 21 09:54:31 r1-hub charon: 08[IKE] <1> received FRAGMENTATION vendor ID Sep 21 09:54:31 r1-hub charon: 08[IKE] <1> received NAT-T (RFC 3947) vendor ID Sep 21 09:54:31 r1-hub charon: 08[IKE] <1> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID Sep 21 09:54:31 r1-hub charon: 08[IKE] <1> 203.0.113.2 is initiating a Main Mode IKE_SA Sep 21 09:54:31 r1-hub charon: 08[CFG] <1> selected proposal: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 Sep 21 09:54:31 r1-hub charon: 08[ENC] <1> generating ID_PROT response 0 [ SA V V V V ] Sep 21 09:54:31 r1-hub charon: 08[NET] <1> sending packet: from 198.51.100.111[500] to 203.0.113.2[500] (160 bytes) Sep 21 09:54:31 r1-hub charon: 09[NET] <1> received packet: from 203.0.113.2[500] to 198.51.100.111[500] (244 bytes) Sep 21 09:54:31 r1-hub charon: 09[ENC] <1> parsed ID_PROT request 0 [ KE No NAT-D NAT-D ] Sep 21 09:54:31 r1-hub charon: 09[IKE] <1> remote host is behind NAT Sep 21 09:54:31 r1-hub charon: 09[ENC] <1> generating ID_PROT response 0 [ KE No NAT-D NAT-D ] Sep 21 09:54:31 r1-hub charon: 09[NET] <1> sending packet: from 198.51.100.111[500] to 203.0.113.2[500] (244 bytes) Sep 21 09:54:31 r1-hub charon: 10[NET] <1> received packet: from 203.0.113.2[4500] to 198.51.100.111[4500] (76 bytes) Sep 21 09:54:31 r1-hub charon: 10[ENC] <1> invalid ID_V1 payload length, decryption failed? Sep 21 09:54:31 r1-hub charon: 10[ENC] <1> could not decrypt payloads Sep 21 09:54:31 r1-hub charon: 10[IKE] <1> message parsing failed Sep 21 09:54:31 r1-hub charon: 10[ENC] <1> generating INFORMATIONAL_V1 request 4092231796 [ HASH N(PLD_MAL) ] Sep 21 09:54:31 r1-hub charon: 10[NET] <1> sending packet: from 198.51.100.111[500] to 203.0.113.2[500] (76 bytes) Sep 21 09:54:31 r1-hub charon: 10[IKE] <1> ID_PROT request with message ID 0 processing failed Sep 21 09:54:34 r1-hub charon: 11[NET] <2> received packet: from 203.0.113.5[500] to 198.51.100.111[500] (216 bytes) Sep 21 09:54:34 r1-hub charon: 11[ENC] <2> parsed ID_PROT request 0 [ SA V V V V V ] Sep 21 09:54:34 r1-hub charon: 11[IKE] <2> received XAuth vendor ID Sep 21 09:54:34 r1-hub charon: 11[IKE] <2> received DPD vendor ID Sep 21 09:54:34 r1-hub charon: 11[IKE] <2> received FRAGMENTATION vendor ID Sep 21 09:54:34 r1-hub charon: 11[IKE] <2> received NAT-T (RFC 3947) vendor ID Sep 21 09:54:34 r1-hub charon: 11[IKE] <2> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID Sep 21 09:54:34 r1-hub charon: 11[IKE] <2> 203.0.113.5 is initiating a Main Mode IKE_SA Sep 21 09:54:34 r1-hub charon: 11[CFG] <2> selected proposal: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 Sep 21 09:54:34 r1-hub charon: 11[ENC] <2> generating ID_PROT response 0 [ SA V V V V ] Sep 21 09:54:34 r1-hub charon: 11[NET] <2> sending packet: from 198.51.100.111[500] to 203.0.113.5[500] (160 bytes) Sep 21 09:54:34 r1-hub charon: 12[NET] <2> received packet: from 203.0.113.5[500] to 198.51.100.111[500] (244 bytes) Sep 21 09:54:34 r1-hub charon: 12[ENC] <2> parsed ID_PROT request 0 [ KE No NAT-D NAT-D ] Sep 21 09:54:34 r1-hub charon: 12[IKE] <2> remote host is behind NAT Sep 21 09:54:34 r1-hub charon: 12[ENC] <2> generating ID_PROT response 0 [ KE No NAT-D NAT-D ] Sep 21 09:54:34 r1-hub charon: 12[NET] <2> sending packet: from 198.51.100.111[500] to 203.0.113.5[500] (244 bytes) Sep 21 09:54:34 r1-hub charon: 15[NET] <2> received packet: from 203.0.113.5[4500] to 198.51.100.111[4500] (76 bytes) Sep 21 09:54:34 r1-hub charon: 15[ENC] <2> invalid ID_V1 payload length, decryption failed? Sep 21 09:54:34 r1-hub charon: 15[ENC] <2> could not decrypt payloads Sep 21 09:54:34 r1-hub charon: 15[IKE] <2> message parsing failed Sep 21 09:54:34 r1-hub charon: 15[ENC] <2> generating INFORMATIONAL_V1 request 2882526405 [ HASH N(PLD_MAL) ]