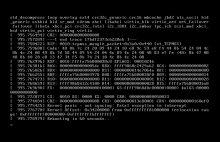
To reproduce this bug.
set policy route MSS-CLAMP rule 10 protocol tcp set policy route MSS-CLAMP rule 10 set tcp-mss pmtu set policy route MSS-CLAMP rule 10 tcp flags SYN set interfaces ethernet eth0 policy route MSS-CLAMP commit
Initiate any TCP session.
vyos@r1-roll:~$ sudo curl https://yahoo.com
Original post https://forum.vyos.io/t/kernel-panic-with-set-mss-pmtu/5850