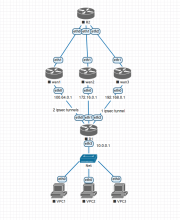
When performing traceroutes from 1.3-rolling-202007300117 pings are round-robin'd through the 3 WAN interfaces despite rule 5 that directs packets through WAN1 by default.
Toggling "enable-local-traffic" has no effect. All traffic from the local box follows the system routes.
load-balancing {
wan {
enable-local-traffic
flush-connections
interface-health eth0 {
nexthop dhcp
test 0 {
resp-time 5
target 8.8.8.8
ttl-limit 1
type ping
}
test 1 {
resp-time 5
target 8.8.4.4
ttl-limit 1
type ping
}
}
interface-health eth1 {
nexthop dhcp
test 0 {
resp-time 5
target 1.1.1.1
ttl-limit 1
type ping
}
test 1 {
resp-time 5
target 1.0.0.1
ttl-limit 1
}
}
interface-health eth2 {
nexthop dhcp
test 0 {
resp-time 5
target 4.2.2.2
ttl-limit 1
type ping
}
test 1 {
resp-time 5
target 4.2.2.1
ttl-limit 1
}
}
rule 5 {
destination {
address 0.0.0.0/0
}
inbound-interface !eth7
failover
interface eth0 {
weight 10
}
interface eth1 {
weight 20
}
interface eth2 {
weight 30
}
protocol all
}
rule 10 {
destination {
address 0.0.0.0/0
}
inbound-interface eth7
interface eth0 {
weight 10
}
interface eth1 {
weight 10
}
interface eth2 {
weight 10
}
protocol all
source {
address 10.0.0.0/16
}
}
sticky-connections {
inbound
}
}
}