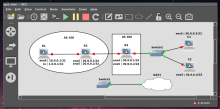
PR with feature request:
https://github.com/vyos/vyos-1x/pull/1555
- Feed Queries
- All Stories
- Search
- Feed Search
- Transactions
- Transaction Logs
All Stories
Sep 22 2022
@sdev @Netboy3 I'll test if the new implementation is done and if the bug is fixed I'll close this PR, thanks
@jack9603301 I've tested your updated PR and it seems to work well now. Thank you for the quick response.
@sdev I've tested your PR and it seems to also fix both issues. I did not test anything beyond DNAT port only in both ip and ip6 families.
Sep 21 2022
Included a fix for this in NAT refactor: https://github.com/vyos/vyos-1x/pull/1552
PR for NAT included with refactor: https://github.com/vyos/vyos-1x/pull/1552
@jack9603301, your PR solves the NAT66 issue - thank you. However, the change you made to nat.py to try to solve the NAT44 issue is not complete and seem to also require a template change. I'll post additional details in the PR.
Since jump action was added, It would be good to also add "return" action
Initial PR here, https://github.com/vyos/vyos-1x/pull/1551.
Sep 20 2022
It seems we have working ISIS segment routing:
@Netboy3 Let me modify the template to support
Sep 19 2022
Why would you enforce an address? It is perfectly OK to have port-only DNAT66 without any destination address such as:
nft add rule ip6 nat PREROUTING iifname eth1 counter tcp dport 443 dnat to :3000
Problem is that the test logic breaks on this and spits out a wrong statement to NFT that barfs on it.
Maybe we should add check to NAT66 to enforce the given address
Sep 18 2022
@n.fort Maybe set firewall name <name> rule <rule> ipsec match-gre? This feels a bit hacky though... Almost like match should be its own block and contain ipsec, none, or gre
Sep 17 2022
It works for me (tm)
PR for VyOS 1.3.3 https://github.com/vyos/vyos-1x/pull/1548
Sep 16 2022
PR https://github.com/vyos/vyos-1x/pull/1545
PR https://github.com/vyos/vyatta-cfg-system/pull/185
set service ids ddos-protection direction 'in' set service ids ddos-protection listen-interface 'eth1' set service ids ddos-protection mode mirror set service ids ddos-protection threshold general fps '1000' set service ids ddos-protection threshold general mbps '200' set service ids ddos-protection threshold general pps '150000' set service ids ddos-protection threshold tcp fps '25' set service ids ddos-protection threshold tcp mbps '55' set service ids ddos-protection threshold tcp pps '155' set service ids ddos-protection threshold udp fps '100' set service ids ddos-protection threshold udp mbps '100' set service ids ddos-protection threshold udp pps '100' set service ids ddos-protection threshold icmp fps '200' set service ids ddos-protection threshold icmp mbps '210' set service ids ddos-protection threshold icmp pps '2040'
Expected fastnermon config entries:
# General threshold ban_for_flows = on threshold_flows = 1000 ban_for_bandwidth = on threshold_mbps = 200 ban_for_pps = on threshold_pps = 150000