Description: "restart ipsec" command does not reinitiate the ipsec connection only in DMVPN setup.
The command "restart ipsec" was executed in the spoke, post which the tunnel goes down and just the new ipsec process is created and no further messages were observed.
Jan 21 11:01:26 charon[4680]: 12[CFG] added vici connection: dmvpn-nhrvpn-tun100 Jan 21 11:01:26 swanctl[4706]: loaded ike secret 'ike-dmvpn-tun100' Jan 21 11:01:26 swanctl[4706]: no authorities found, 0 unloaded Jan 21 11:01:26 swanctl[4706]: no pools found, 0 unloaded Jan 21 11:01:26 swanctl[4706]: loaded connection 'dmvpn-nhrvpn-tun100' Jan 21 11:01:26 swanctl[4706]: successfully loaded 1 connections, 0 unloaded Jan 21 11:01:26 systemd[1]: Started strongSwan IPsec IKEv1/IKEv2 daemon using swanctl.
Restarting the opennhrp and strongswan service also does not initiate the ipsec connection.
sudo systemctl restart opennhrp sudo systemctl restart strongswan
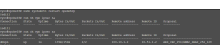
In the hub, I notice the child-sa gets created but again being deleted:
Loading configuration brings the ipsec connection back i.e committing any changes related to ipsec.
Jan 21 11:01:26 systemd[1]: Started strongSwan IPsec IKEv1/IKEv2 daemon using swanctl. Jan 21 12:12:21 systemd[1]: Reloading strongSwan IPsec IKEv1/IKEv2 daemon using swanctl... Jan 21 12:12:21 charon[4680]: 05[CFG] loaded 0 entries for attr plugin configuration Jan 21 12:12:21 swanctl[6395]: loaded connection 'dmvpn-nhrvpn-tun100' Jan 21 12:12:21 swanctl[6395]: successfully loaded 1 connections, 0 unloaded Jan 21 12:12:21 systemd[1]: Reloaded strongSwan IPsec IKEv1/IKEv2 daemon using swanctl. Jan 21 12:12:26 charon[4680]: 05[CFG] vici initiate CHILD_SA 'dmvpn', me 10.53.0.2, other 100.10.1.2, limits 0 Jan 21 12:12:26 charon-systemd[4680]: vici initiate CHILD_SA 'dmvpn', me 10.53.0.2, other 100.10.1.2, limits 0 Jan 21 12:12:26 charon-systemd[4680]: initiating IKE_SA dmvpn-nhrvpn-tun100[1] to 100.10.1.2
Is their a logic behind which does not initiate the connection in the DMVPN setup ?
Attached the configuratioon for reference.