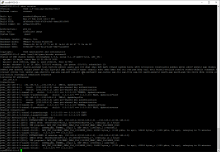
VYOS 1.4 release no longer displayes output for 'sudo ipsec statusall'
currently running 1.4-rolling-202302270317
vyos@VYOS-03:~$ show system image The system currently has the following image(s) installed: 1: 1.4-rolling-202302270317 (default boot) (running image) vyos@VYOS-03:~$
When issuing the command as below, zero output is displayed
vyos@VYOS-03:~$ sudo ipsec statusall vyos@VYOS-03:~$
Before i upgraded to 1.4 rolling release, i was running an older vyos 1.3 release and the output is displayed as expected, as below.
vyos@VYOS-03:~$ sudo ipsec statusall
Status of IKE charon daemon (strongSwan 5.9.1, Linux 5.15.67-amd64-vyos, x86_64):
uptime: 2 days, since Dec 10 12:44:57 2022
malloc: sbrk 2109440, mmap 0, used 1623184, free 486256
worker threads: 11 of 16 idle, 5/0/0/0 working, job queue: 0/0/0/0, scheduled: 10
loaded plugins: charon test-vectors ldap pkcs11 tpm aesni aes rc2 sha2 sha1 md5 mgf1 rdrand random nonce x509 revocation constraints pubkey pkcs1 pkcs7 pkcs8 pkcs12 pgp dnskey sshkey pem openssl gcrypt af-alg fips-prf gmp curve25519 agent chapoly xcbc cmac hmac ctr ccm gcm drbg curl attr kernel-netlink resolve socket-default connmark stroke vici updown eap-identity eap-aka eap-md5 eap-gtc eap-mschapv2 eap-radius eap-tls eap-ttls eap-tnc xauth-generic xauth-eap xauth-pam tnc-tnccs dhcp lookip error-notify certexpire led addrblock counters
Listening IP addresses:
192.168.6.5
Connections:
peer_192-168-6-1: 192.168.6.5...192.168.6.1 IKEv2, dpddelay=30s
peer_192-168-6-1: local: [192.168.6.5] uses pre-shared key authentication
peer_192-168-6-1: remote: [192.168.6.1] uses pre-shared key authentication
peer_192-168-6-1_tunnel_0: child: 0.0.0.0/0 === 0.0.0.0/0 TUNNEL, dpdaction=clear
peer_192-168-6-1_tunnel_0_passthrough: child: 0.0.0.0/0 === 0.0.0.0/0 PASS, dpdaction=clear
peer_192-168-6-3: 192.168.6.5...192.168.6.3 IKEv2, dpddelay=30s
peer_192-168-6-3: local: [192.168.6.5] uses pre-shared key authentication
peer_192-168-6-3: remote: [192.168.6.3] uses pre-shared key authentication
peer_192-168-6-3_tunnel_0: child: 0.0.0.0/0 === 0.0.0.0/0 TUNNEL, dpdaction=clear
peer_192-168-6-3_tunnel_0_passthrough: child: 0.0.0.0/0 === 0.0.0.0/0 PASS, dpdaction=clear
Shunted Connections:
peer_192-168-6-1_tunnel_0_passthrough: 0.0.0.0/0 === 0.0.0.0/0 PASS
peer_192-168-6-3_tunnel_0_passthrough: 0.0.0.0/0 === 0.0.0.0/0 PASS
Security Associations (2 up, 0 connecting):
peer_192-168-6-1[54]: ESTABLISHED 28 minutes ago, 192.168.6.5[192.168.6.5]...192.168.6.1[192.168.6.1]
peer_192-168-6-1[54]: IKEv2 SPIs: bb1f8c32c3182ca3_i e8bcfe736960bac5_r*, rekeying in 80 minutes
peer_192-168-6-1[54]: IKE proposal: AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
peer_192-168-6-1_tunnel_0{121}: INSTALLED, TUNNEL, reqid 2, ESP SPIs: c0671dd7_i c5386c5f_o
peer_192-168-6-1_tunnel_0{121}: AES_CBC_256/HMAC_SHA2_256_128, 36551 bytes_i (728 pkts, 1s ago), 35837 bytes_o (731 pkts, 1s ago), rekeying in 31 minutes
peer_192-168-6-1_tunnel_0{121}: 0.0.0.0/0 === 0.0.0.0/0
peer_192-168-6-3[53]: ESTABLISHED 28 minutes ago, 192.168.6.5[192.168.6.5]...192.168.6.3[192.168.6.3]
peer_192-168-6-3[53]: IKEv2 SPIs: 2ba14106a6db5b57_i 4a7da4eef711cc6f_r*, rekeying in 87 minutes
peer_192-168-6-3[53]: IKE proposal: AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
peer_192-168-6-3_tunnel_0{120}: INSTALLED, TUNNEL, reqid 1, ESP SPIs: c8fda383_i c7ac3eac_o
peer_192-168-6-3_tunnel_0{120}: AES_CBC_256/HMAC_SHA2_256_128, 36374 bytes_i (725 pkts, 1s ago), 35717 bytes_o (728 pkts, 1s ago), rekeying in 31 minutes
peer_192-168-6-3_tunnel_0{120}: 0.0.0.0/0 === 0.0.0.0/0
root@VYOS-03:/home/vyos# swanctl -l
peer_192-168-6-1: #54, ESTABLISHED, IKEv2, bb1f8c32c3182ca3_i e8bcfe736960bac5_r*
local '192.168.6.5' @ 192.168.6.5[500]
remote '192.168.6.1' @ 192.168.6.1[500]
AES_CBC-256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
established 1689s ago, rekeying in 4825s
peer_192-168-6-1_tunnel_0: #121, reqid 2, INSTALLED, TUNNEL, ESP:AES_CBC-256/HMAC_SHA2_256_128
installed 1689s ago, rekeying in 1911s, expires in 1911s
in c0671dd7 (-|0x00000001), 36650 bytes, 730 packets, 2s ago
out c5386c5f (-|0x00000001), 35936 bytes, 733 packets, 2s ago
local 0.0.0.0/0
remote 0.0.0.0/0
peer_192-168-6-3: #53, ESTABLISHED, IKEv2, 2ba14106a6db5b57_i 4a7da4eef711cc6f_r*
local '192.168.6.5' @ 192.168.6.5[500]
remote '192.168.6.3' @ 192.168.6.3[500]
AES_CBC-256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
established 1690s ago, rekeying in 5241s
peer_192-168-6-3_tunnel_0: #120, reqid 1, INSTALLED, TUNNEL, ESP:AES_CBC-256/HMAC_SHA2_256_128
installed 1690s ago, rekeying in 1910s, expires in 1910s
in c8fda383 (-|0x00000002), 36532 bytes, 728 packets, 0s ago
out c7ac3eac (-|0x00000002), 35856 bytes, 731 packets, 0s ago
local 0.0.0.0/0
remote 0.0.0.0/0
vyos@VYOS-03:~$