There is a report from the forum
I configured 20,000 firewall rules on my vyos(48 cores and 100GB RAN, KVM), but commit configuration need at least 3 hours,and after I reboot my vyos machine, it can not up and stagnate at “Mouting Vyos Config ”
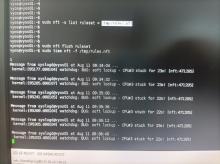
If use nftables natively as:
sudo nft -s list ruleset > /tmp/rules.nft sudo nft flush ruleset sudo time nft -f /tmp/rules.nft
It takes almost 10 hours