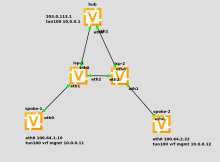
Add ability to configure DMVPN in vrf context.
It works if spoke1 mGRE tun100 interface in vrf, and external interface eth0 without vrf.
It doesn't work if tun100 and eth0 are in different vrf's.
Spoke01 configuration:
set interfaces ethernet eth0 address '100.64.1.10/24' set interfaces ethernet eth0 description 'External-link' set interfaces tunnel tun100 address '10.0.0.11/24' set interfaces tunnel tun100 encapsulation 'gre' set interfaces tunnel tun100 multicast 'enable' set interfaces tunnel tun100 parameters ip key '1' set interfaces tunnel tun100 source-address '0.0.0.0' set interfaces tunnel tun100 vrf 'mgmt' set protocols nhrp tunnel tun100 cisco-authentication 'secret' set protocols nhrp tunnel tun100 holding-time '300' set protocols nhrp tunnel tun100 map 10.0.0.1/24 nbma-address '203.0.113.1' set protocols nhrp tunnel tun100 map 10.0.0.1/24 register set protocols nhrp tunnel tun100 multicast 'nhs' set protocols nhrp tunnel tun100 redirect set protocols nhrp tunnel tun100 shortcut set vpn ipsec esp-group ESP-HUB compression 'disable' set vpn ipsec esp-group ESP-HUB lifetime '1800' set vpn ipsec esp-group ESP-HUB mode 'transport' set vpn ipsec esp-group ESP-HUB pfs 'dh-group2' set vpn ipsec esp-group ESP-HUB proposal 1 encryption 'aes256' set vpn ipsec esp-group ESP-HUB proposal 1 hash 'sha1' set vpn ipsec esp-group ESP-HUB proposal 2 encryption '3des' set vpn ipsec esp-group ESP-HUB proposal 2 hash 'md5' set vpn ipsec ike-group IKE-HUB close-action 'none' set vpn ipsec ike-group IKE-HUB ikev2-reauth 'no' set vpn ipsec ike-group IKE-HUB key-exchange 'ikev1' set vpn ipsec ike-group IKE-HUB lifetime '3600' set vpn ipsec ike-group IKE-HUB proposal 1 dh-group '2' set vpn ipsec ike-group IKE-HUB proposal 1 encryption 'aes256' set vpn ipsec ike-group IKE-HUB proposal 1 hash 'sha1' set vpn ipsec ike-group IKE-HUB proposal 2 dh-group '2' set vpn ipsec ike-group IKE-HUB proposal 2 encryption 'aes128' set vpn ipsec ike-group IKE-HUB proposal 2 hash 'sha1' set vpn ipsec interface 'eth0' set vpn ipsec profile NHRPVPN authentication mode 'pre-shared-secret' set vpn ipsec profile NHRPVPN authentication pre-shared-secret 'secret' set vpn ipsec profile NHRPVPN bind tunnel 'tun100' set vpn ipsec profile NHRPVPN esp-group 'ESP-HUB' set vpn ipsec profile NHRPVPN ike-group 'IKE-HUB' set vrf bind-to-all set vrf name mgmt table '100'
Ping from spoke1 => spoke2:
vyos@spoke-1:~$ ping 10.0.0.12 vrf mgmt count 5 PING 10.0.0.12 (10.0.0.12) 56(84) bytes of data. 64 bytes from 10.0.0.12: icmp_seq=1 ttl=64 time=1.27 ms 64 bytes from 10.0.0.12: icmp_seq=2 ttl=64 time=1.55 ms 64 bytes from 10.0.0.12: icmp_seq=3 ttl=64 time=1.08 ms
If I attach vrf "FOO" to eth0 interface, IPSec can't establish Phase1
vyos@spoke-1:~$ sudo swanctl -l (unnamed): #14, CONNECTING, IKEv1, 057faeb8c6e55899_i 49912e089f7bac47_r* local '%any' @ 100.64.1.10[500] remote '%any' @ 203.0.113.1[500] AES_CBC-256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 passive: ISAKMP_VENDOR MAIN_MODE ISAKMP_NATD dmvpn-NHRPVPN-tun100: #1, CONNECTING, IKEv1, 590e9bdc549b80ca_i* 0000000000000000_r local '%any' @ 100.64.1.10[500] remote '%any' @ 203.0.113.1[500] queued: QUICK_MODE active: ISAKMP_VENDOR ISAKMP_CERT_PRE MAIN_MODE ISAKMP_CERT_POST ISAKMP_NATD vyos@spoke-1:~$