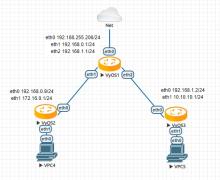
Here's configuration of 3 routers (one - gateway, others - points of IPSec connection)
Gateway
set system host-name Gateway set interfaces ethernet eth0 address dhcp set interfaces ethernet eth0 description 'OUTSIDE' set interfaces ethernet eth1 address '192.168.0.1/24' set interfaces ethernet eth1 description 'LAN1' set interfaces ethernet eth2 address '192.168.1.1/24' set interfaces ethernet eth2 description 'LAN2' set service dhcp-server shared-network-name LAN1 subnet 192.168.0.0/24 default-router '192.168.0.1' set service dhcp-server shared-network-name LAN1 subnet 192.168.0.0/24 dns-server '192.168.0.1' set service dhcp-server shared-network-name LAN1 subnet 192.168.0.0/24 domain-name 'vyos.net' set service dhcp-server shared-network-name LAN1 subnet 192.168.0.0/24 lease '86400' set service dhcp-server shared-network-name LAN1 subnet 192.168.0.0/24 range 0 start 192.168.0.9 set service dhcp-server shared-network-name LAN1 subnet 192.168.0.0/24 range 0 stop '192.168.0.254' set nat source rule 100 outbound-interface 'eth0' set nat source rule 100 source address '192.168.0.0/23' set nat source rule 100 translation address masquerade
R1
set system host-name R1 set interfaces ethernet eth0 address dhcp set interfaces ethernet eth0 description 'gateway' set interfaces ethernet eth1 address '172.16.0.1/24' set interfaces ethernet eth1 description 'LAN' set vpn ipsec esp-group london-berlin-esp compression 'disable' set vpn ipsec esp-group london-berlin-esp lifetime '1800' set vpn ipsec esp-group london-berlin-esp mode 'tunnel' set vpn ipsec esp-group london-berlin-esp pfs 'enable' set vpn ipsec esp-group london-berlin-esp proposal 1 encryption 'aes256' set vpn ipsec esp-group london-berlin-esp proposal 1 hash 'sha1' set vpn ipsec ike-group london-berlin-ike ikev2-reauth 'no' set vpn ipsec ike-group london-berlin-ike key-exchange 'ikev1' set vpn ipsec ike-group london-berlin-ike lifetime '3600' set vpn ipsec ike-group london-berlin-ike proposal 1 encryption 'aes256' set vpn ipsec ike-group london-berlin-ike proposal 1 hash 'sha1' set vpn ipsec ike-group london-berlin-ike proposal 1 dh-group 2 set vpn ipsec ipsec-interfaces interface 'eth0' set vpn ipsec site-to-site peer 192.168.1.2 authentication id @R1 set vpn ipsec site-to-site peer 192.168.1.2 authentication mode 'pre-shared-secret' set vpn ipsec site-to-site peer 192.168.1.2 authentication pre-shared-secret 'SomePreSharedKey' set vpn ipsec site-to-site peer 192.168.1.2 ike-group 'london-berlin-ike' set vpn ipsec site-to-site peer 192.168.1.2 connection-type initiate set vpn ipsec site-to-site peer 192.168.1.2 dhcp-interface 'eth0' set vpn ipsec site-to-site peer 192.168.1.2 tunnel 0 allow-nat-networks 'disable' set vpn ipsec site-to-site peer 192.168.1.2 tunnel 0 allow-public-networks 'disable' set vpn ipsec site-to-site peer 192.168.1.2 tunnel 0 esp-group 'london-berlin-esp' set vpn ipsec site-to-site peer 192.168.1.2 tunnel 0 local prefix '172.16.0.0/24' set vpn ipsec site-to-site peer 192.168.1.2 tunnel 0 remote prefix '10.10.10.0/24' set nat source rule 100 outbound-interface 'eth0' set nat source rule 100 source address '172.16.0.0/24' set nat source rule 100 translation address masquerade set protocols static route 0.0.0.0/0 next-hop 192.168.0.1
R2
set system host-name R2 set interfaces ethernet eth0 address '192.168.1.2/24' set interfaces ethernet eth0 description 'gateway' set interfaces ethernet eth1 address '10.10.10.1/24' set interfaces ethernet eth1 description 'LAN' set vpn ipsec esp-group london-berlin-esp compression 'disable' set vpn ipsec esp-group london-berlin-esp lifetime '1800' set vpn ipsec esp-group london-berlin-esp mode 'tunnel' set vpn ipsec esp-group london-berlin-esp pfs 'enable' set vpn ipsec esp-group london-berlin-esp proposal 1 encryption 'aes256' set vpn ipsec esp-group london-berlin-esp proposal 1 hash 'sha1' set vpn ipsec ike-group london-berlin-ike ikev2-reauth 'no' set vpn ipsec ike-group london-berlin-ike key-exchange 'ikev1' set vpn ipsec ike-group london-berlin-ike lifetime '3600' set vpn ipsec ike-group london-berlin-ike proposal 1 encryption 'aes256' set vpn ipsec ike-group london-berlin-ike proposal 1 hash 'sha1' set vpn ipsec ike-group london-berlin-ike proposal 1 dh-group 2 set vpn ipsec ipsec-interfaces interface 'eth0' set vpn ipsec site-to-site peer @R1 authentication mode 'pre-shared-secret' set vpn ipsec site-to-site peer @R1 authentication pre-shared-secret 'SomePreSharedKey' set vpn ipsec site-to-site peer @R1 ike-group 'london-berlin-ike' set vpn ipsec site-to-site peer @R1 connection-type respond set vpn ipsec site-to-site peer @R1 authentication remote-id @R1 set vpn ipsec site-to-site peer @R1 local-address '192.168.1.2' set vpn ipsec site-to-site peer @R1 tunnel 0 allow-nat-networks 'disable' set vpn ipsec site-to-site peer @R1 tunnel 0 allow-public-networks 'disable' set vpn ipsec site-to-site peer @R1 tunnel 0 esp-group 'london-berlin-esp' set vpn ipsec site-to-site peer @R1 tunnel 0 local prefix '10.10.10.0/24' set vpn ipsec site-to-site peer @R1 tunnel 0 remote prefix '172.16.0.0/24' set nat source rule 100 outbound-interface 'eth0' set nat source rule 100 source address '10.10.10.0/24' set nat source rule 100 translation address masquerade set protocols static route 0.0.0.0/0 next-hop 192.168.1.1
Tunnel is up
vyos@R1:~$ show vpn ike sa
Peer ID / IP Local ID / IP
------------ -------------
192.168.1.2 192.168.1.2 192.168.0.9 R1
State IKEVer Encrypt Hash D-H Group NAT-T A-Time L-Te
----- ------ ------- ---- --------- ----- ------ ----
up IKEv1 AES_CBC_256 HMAC_SHA1_96 MODP_1024 no 30 0
vyos@R1:~$ show vpn ipsec sa
Connection State Uptime Bytes In/Out Packets In/Out l
------------------------- ------- -------- -------------- ---------------- -
peer-192.168.1.2-tunnel-0 up 37s 0B/0B 0/0 4Here's what we have from sudo swanctl -L
peer-192.168.1.2-tunnel-0: , no reauthentication, no rekeying
local: ['192.168.0.9/24'
local: fe80::5210:ff:fe02:0/64
local: ]
remote: 192.168.1.2
local pre-shared key authentication:
id: R1
remote pre-shared key authentication:
id: 192.168.1.2
peer-192.168.1.2-tunnel-0: TUNNEL, rekeying every 1260s
local: 172.16.0.0/24
remote: 10.10.10.0/24And sudo ip -6 a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 state UNKNOWN qlen 1000
inet6 fe80::200:ff:fe00:0/64 scope link
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 fe80::5210:ff:fe02:0/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 fe80::5210:ff:fe02:1/64 scope link
valid_lft forever preferred_lft forever
4: eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 fe80::5210:ff:fe02:2/64 scope link
valid_lft forever preferred_lft forever
5: eth3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 fe80::5210:ff:fe02:3/64 scope link
valid_lft forever preferred_lft foreverAlso files:
/etc/ipsec.conf
# Created by VyOS - manual changes will be overwritten
config setup
charondebug = ""
uniqueids = yes
conn peer-192.168.1.2
authby = secret
left = ['192.168.0.9/24', 'fe80::5210:ff:fe02:0/64'] # dhcp:eth0
leftid = "@R1"
right = 192.168.1.2
keylife = 3600s
rekeymargin = 540s
keyexchange = ikev1
ike = aes256-sha1-modp1024!
ikelifetime = 3600s
reauth = no
closeaction = none
conn peer-192.168.1.2-tunnel-0
also = peer-192.168.1.2
leftsubnet = 172.16.0.0/24[%any/%any]
rightsubnet = 10.10.10.0/24[%any/%any]
esp = aes256-sha1-modp1024!
keylife = 1800s
compress = no
type = tunnel
auto = start
keyingtries = %forever
conn peer-192.168.1.2-tunnel-0-passthough
left = ['192.168.0.9/24', 'fe80::5210:ff:fe02:0/64']
right = 192.168.1.2
leftsubnet = 172.16.0.0/24
rightsubnet = 172.16.0.0/24
type = passthrough
authby = never
auto = routeand /etc/ipsec.secret
# Created by VyOS - manual changes will be overwritten ['192.168.0.9/24', 'fe80::5210:ff:fe02:0/64'] 192.168.1.2 @R1 : PSK "SomePreSharedKey" # dhcp:eth0