In 1.2 this was the only way to 'Do not nat traffic destined to RFC1918 addresses'
set nat source rule 1 destination address '192.168.0.0/16' set nat source rule 1 exclude set nat source rule 1 outbound-interface 'any' set nat source rule 2 destination address '10.0.0.0/8' set nat source rule 2 exclude set nat source rule 2 outbound-interface 'any' set nat source rule 3 destination address '172.16.0.0/12' set nat source rule 3 exclude set nat source rule 3 outbound-interface 'any' set nat source rule 4 outbound-interface 'eth0.115' set nat source rule 4 source address '10.40.0.0/24' set nat source rule 4 translation address '99.99.99.99'
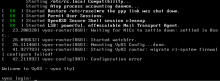
However, with recent changes in nat, there are two problems:
- 'outbound-interface any' no longer exists, and it generates a warning "NAT configuration warning: interface any does not exist on this system"
- An rule with 'exclude' now requires a translation address "Source NAT configuration error in rule 1: translation address not specified"
This means that this rule in 1.3 does not work:
set nat source rule 1 destination address '192.168.0.0/16' set nat source rule 1 exclude set nat source rule 1 outbound-interface 'any' set nat source rule 1 translation address 'masquerade'
It generates an iptables rule of "-A POSTROUTING -d 192.168.0.0/16 -o any -m comment --comment DST-NAT-1 -j RETURN" - and I also notice that it's called 'DST-NAT-1' instead of SRC-NAT-1, too.
The complete rules generated by 1.2 are:
*nat :PREROUTING ACCEPT [3217:945646] :INPUT ACCEPT [307:21920] :OUTPUT ACCEPT [227:15740] :POSTROUTING ACCEPT [229:15847] :VYATTA_PRE_DNAT_HOOK - [0:0] :VYATTA_PRE_SNAT_HOOK - [0:0] -A PREROUTING -j VYATTA_PRE_DNAT_HOOK -A POSTROUTING -j VYATTA_PRE_SNAT_HOOK -A POSTROUTING -d 192.168.0.0/16 -m comment --comment SRC-NAT-1 -j RETURN -A POSTROUTING -d 10.0.0.0/8 -m comment --comment SRC-NAT-2 -j RETURN -A POSTROUTING -d 172.16.0.0/12 -m comment --comment SRC-NAT-3 -j RETURN -A POSTROUTING -s 10.40.0.0/24 -o eth0.115 -m comment --comment SRC-NAT-4 -j SNAT --to-source 99.99.99.99 -A VYATTA_PRE_DNAT_HOOK -j RETURN -A VYATTA_PRE_SNAT_HOOK -j RETURN COMMIT